U.S. healthcare organizations may be inadequately prepared to deal with security challenges and the requirements of the American Recovery and Reinvestment Act (ARRA) to maintain privacy and security of patient health data, according to the second annual security survey of the Healthcare Information and Management Systems Society (HIMSS).
The 2009 HIMSS Security Survey results were released November 3, revealing that for the second year in a row, the majority of healthcare organization respondents have not made healthcare IT security a top priority. If the information provided by the 196 chief information officers, security managers, and senior information technology executives is representative, healthcare facilities in the U.S. are woefully underutilizing available security technologies, are vulnerable to security breaches, and are unprepared to deal with them.
Statistics about healthcare IT security measures are seldom published, and this survey provides a rare glimpse into a vitally important subject. But the ability to generalize survey results is limited by the fact that out of 4,500 healthcare IT executives invited by HIMSS to complete the Web-based survey, only 4.4% took the time to respond. The response in 2008 to the first survey, also underwritten as an educational grant from Symantec of Mountain View, CA, was equally lackluster.
So -- why aren't hospitals better prepared?
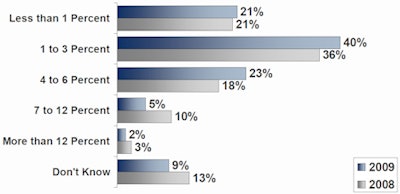
Budgets, or lack thereof, remain a critical source of the problem. Twenty-one percent of the respondent hospitals spent less than 1% of their organization's annual IT budget on information security, while 40% spent between 1% and 3%, and 23% spent between 4% and 6%. Budgeted investment in maintaining IT security remained unchanged from 2008, according to HIMSS.
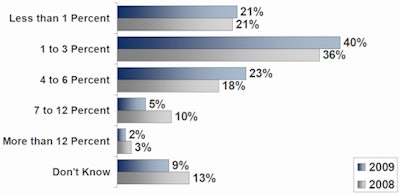 |
| Percent of IT budget dedicated to information security. Image courtesy of 2009 HIMSS Security Survey. |
Security IT industry professionals recommend that hospitals conduct formal, comprehensive risk analyses to identify security vulnerabilities on at least an annual basis for small hospitals, and on a semiannual or quarterly basis for medium-to-large hospitals and multifacility enterprise organizations. Formal risk analyses can find vulnerabilities to security breaches, enabling them to be categorized by type and level of importance.
However, the 2009 HIMSS Security Survey revealed that only 8% of respondents conducted external risk analysis, vulnerability analysis, and/or penetration testing every six months, and only another 47% on an annual basis. Three-fourths of these respondents, including the 31% who conducted risk analyses every two years or longer intervals, admitted that these security assessments identified patient data at risk due to inadequate security controls, policies, and procedures within their healthcare institutions.
Although nearly all respondents reported that their organizations share patient data in an electronic format, primarily with government agencies, only 67% of responding organizations said that they used encryption to secure data in transmission. Fewer than half reported encrypting data stored in archives.
Almost all (94%) respondents reported that their organizations collect and analyze information in audit logs, with 83% reviewing firewall logs. Seventy-five percent also analyze information from their application software logs and servers, and 69% collect and analyze data from intrusion-detection systems. However, the majority reviewed this data manually; only 25% reported that they perform electronic analysis of the data they collect.
Types of events captured by audit logs included security-critical events (81%), clinician access to data (72%), and nonclinician access to data (64%). While approximately half of the healthcare organizations surveyed allow patients to access electronic patient information, including diagnostic examination scheduling or results, and/or laboratory testing results, only 12% analyze the audit data logs from this patient access.
The survey also revealed that 40% of the respondents who monitored audit logs do not measure the success of their controls. More than half (57%) of the total number of respondents who measured the effectiveness of their security reported that they evaluated reduced risk exposure, primarily by identifying the number of detected security incidents. Only 8% reported that they measured return on investment of the cost of security tools when compared to the risk reduction they were able to identify.
Only half of the respondents had a plan in place for responding to threats or incidents related to a security breach. Three-quarters of the respondents reported that they did not have a plan in place to deal with data loss.
The 2009 HIMSS Security Survey did not include any questions specifically relating to security protection of medical devices or PACS. While respondents were asked about the number of medical identity threats (33% reported one or more known cases), no questions were specifically asked about virus infestations, such as the Conficker virus. This virus was positively identified as having infiltrated hundreds of healthcare facilities as well as hundreds of PACS worldwide in the first half of 2009.
By Cynthia E. Keen
AuntMinnie.com staff writer
November 12, 2009
Related Reading
FDA issues cybersecurity reminder, November 9, 2009
UNC research server hit by hacker attack, September 29, 2009
Conficker worm highlights PACS cybersecurity issues, June 2, 2009
IT networks shut down at three London hospitals, November 26, 2008
Intrusion-detection testing finds network vulnerabilities, August 11, 2008
Copyright © 2009 AuntMinnie.com



















